Web Service User Security
Users of the PrismHR API are strongly encouraged to make full use of the web service user security settings described in this document.
Basic Security Settings
On the Web Service User form, you can configure a number of security settings to restrict the capabilities of API users:
| • | Access to API versions |
| • | Access to specific lists of clients |
| • | Access to lists of IP addresses |
| • | Access to API endpoints (this can be restricted further to a specific time range) |
Version, Client, and IP Security
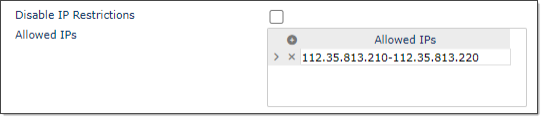
Use the Minimum API Version field to prevent your user from accessing older versions of the API.
Note: prismhr-api corresponds to version 2.0+
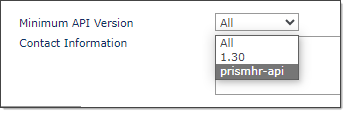
Use the Company Access grid to control the client access of API users. You can deny access to all clients except those in the list, or grant access to all clients except those in the list.
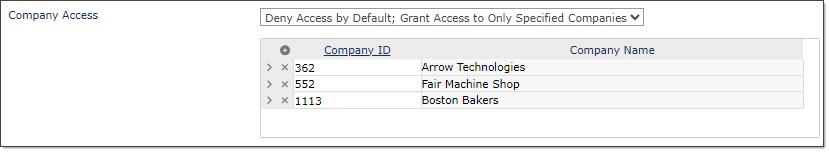
Use the Allowed IPs grid to control the IP addresses from which this user can make API calls. You can also enter an IP range if necessary.
Note: The option to Disable IP Restrictions is intended for development purposes only. Do not enable this setting in production.
Access Control Options for Allowed Methods
Many Allowed Methods support their own specific security settings, providing you with additional ways to fine-tune the data access of your web service users. The three main types are:
| • | PII Unmasking |
| • | Option-level access control |
| • | Field-level access control |
PII Unmasking
Example: EmployeeService.getEmployee#NOMASKSSN|NOMASKDOB
By default, the API always returns certain sensitive data fields as asterisks. For example, an ssn value would return as "***-**-****".
You can apply different NOMASK options to reveal the data in these fields. The different NOMASK options correspond to different categories of PII.
In the example above, Social Security Numbers and dates of birth would be returned in full. See this article on the API documentation website for details about unmasking PII.
Option-level access control
Example: EmployeeService.getEmployee#PERSON|CLIENT|COMPENSATION
These settings enable you to control the possible categories of data that can be retrieved with an Allowed Method. For example, you might want to restrict a web service user so they can only pull employee personal details (PERSON), while denying access to the employee's pay details (COMPENSATION).
These settings can only be applied to specific Allowed Methods. A complete list is located on the API documentation website. The article lists them in reverse chronological order of release.
Field-level access control
Example: EmployeeService.updateEmployeeFields#DENY|birthDate|reportsTo
Similar to option-level access control, these settings grant or deny the ability to modify specific data fields.
For a complete list of valid fields, see this article on the API documentation website.
Best Practices
PrismHR encourages you to observe all the web service user best practices described in the [link to WSU Best Practices] article.
In short, we encourage you to:
| 1. | Review all web service users periodically and remove or inactivate any users you no longer need. |
| 2. | Avoid entering or saving the web service user password in the Contact Information field. |
| 3. | Set up Pending Approval Emails for permission updates. See Setting up Approval Emails for Pending Updates to Web Service Users. |
| 4. | Make sure your passwords meet your company’s secure password policies. Notify vendors and partners before password changes. |
| 5. | Use all available web service user security features, including IP restrictions, endpoint restrictions, and option-level security. |
| 6. | Create a unique web service user for each integration so you can customize the security settings. |
