Security Best Practices
System Security Features
You can use PrismHR security features to mitigate risk, including multi-factor authentication (MFA), direct deposit change notifications, password expiration and complexity settings, Internet Protocol (IP) whitelisting, and several audit reports.
Multi-Factor Authentication (MFA)
Enabling MFA offers an additional layer of security to verify a user’s identity and prevent unauthorized access to employee data. In addition to a username and password, MFA requires one more method of authentication to verify the user’s identity before login access is granted on a particular device. The system sends a generated code to the user’s email account or mobile device through SMS text messaging to further verify the user's identity. If enabled, the MFA process triggers when it does not recognize the browser or device attempting to login, or if a set number of days have passed since the last MFA attempt.
In PrismHR, your organization can enable multi-factor authentication at the system, client, or user level. Enabling MFA at the system level affects all service provider, worksite manager, and worksite trusted advisor users. A separate option is also available for employees accessing Employee Portal (EP).
To enable MFA at the system level, use the Authentication Services form (Back Office > System Parameters > Action Menu > Authentication Services) in PrismHR:

Service Providers
MFA is enabled by default for all service provider users in PrismHR. For more information, please see Enabling Multi-Factor Authentication for Service Provider Users.
SMB Clients
MFA can be set up for all your clients or on an individual client basis. MFA is enabled automatically for all worksite managers and trusted advisors. All new managers and advisors will have MFA enabled by default.
Direct Deposit Notification
You can configure ClientSpace to notify employees when a change is made to their direct deposit information. These notifications can help worksite employees and service providers be more proactive in detecting and preventing fraud attempts.
Enforce Strong Passwords
A strong password is the foundation of system security. Strong passwords consist of at least six characters and are a combination of numbers, letters, and symbols. PrismHR passwords can be case-sensitive—both uppercase and lowercase letters are recommended.
Ensure your passwords for superusers and managers are sufficiently complex. You can encourage or even require your users to change passwords periodically. For help with passwords, use a password-generation resource such as strongpasswordgenerator.com and a password management solution such as lastpass.com.
In PrismHR, you can require the use of punctuation with passwords and set password expiration limits using the Authentication Services form (Back Office > System Parameters > Action Menu > Authentication Services).
Be Suspicious
Educate your users to be wary of emails with embedded links or attachments of any kind. While they may look legitimate, clicking a link or attachment can hand over access to your computer to hackers.
Phishing efforts often include requests for account credentials from what appears to be a co-worker. Once a hacker has access to your computer, all your stored passwords may be available.
Restrict User Access
In PrismHR, you can restrict individual user access to specific IP addresses or a range of addresses. This means that any device (computer, mobile phone, tablet) in your network must come from an approved IP address. By restricting user access, you limit the devices and networks with access to PrismHR, making it much more difficult for an outsider to gain entry to the system.
Audit Reports
PrismHR has robust reporting features that can help tip you off to suspicious activity. PrismHR strongly recommends that you run the following reports:
|
•
|
Employee ACH Information and ACH Journal |
|
•
|
Checking Accounts and ACH Originators |
|
•
|
Client Banking Information |
|
•
|
Sensitive Information Changes Report |
When you inspect your reports, look for an unusual number of changes, or for account numbers/transit numbers that are the same or very similar. Confirm that any changes are accurate. Fraudulent fund transfers are typically initiated and tested in small amounts just before a large sum is removed from the system.
Additionally, PrismHR recommends a review of all ACH audit records, ideally right before the ACH files are transmitted. This will confirm that nothing was altered during the business day. Even one change that was not authorized can indicate a vulnerability.
Report Instructions
PrismHR strongly recommends that you run these reports. To check that changes are legitimate, run the same report (Find All Changes to a File) with different parameters (below).
Employee ACH Information and ACH Journal
|
1.
|
Select System Administration > File > Audit Control Maintenance > File Audit Reports > Find Changes to a File Report. |
|
2.
|
In the Audited Filename field, enter one of the following: |
|
•
|
To run the report for employee ACH information, enter EMPLOYEE.ACH. |
|
•
|
To run the report on the ACH journals, enter ACH.JOURNAL. |
|
3.
|
Leave the Audited Record ID and Audited Fieldname fields blank. |
|
•
|
If running the report first thing in the morning, enter the previous day in the first Update date range field, and then enter T in the second field to indicate today's date. |
|
•
|
If running the report in the evening, enter T in both fields to see all changes made today. |
|
5.
|
Leave Optional Company ID blank. |
|
6.
|
Click F2-Create Report. |
Carefully review any changes in numeric fields (account numbers, transit numbers, and so on). Check for:
|
•
|
Activity that occurs extremely late or extremely early in the day. This activity is suspicious. |
|
•
|
Changes from direct deposit of funds to Green Dot Bank or American Express pre-paid cards. These modifications require extra scrutiny to ensure they are legitimate. |
Checking Accounts and ACH Originators
|
1.
|
Select System Administration > File > Audit Control Maintenance > File Audit Reports > Find Changes to a File Report. |
|
2.
|
In the Audited Filename field, enter one of the following: |
|
•
|
To run the report for checking accounts, enter CHECKING.ACCOUNTS. |
|
•
|
To run the report on the ACH origination accounts, enter ACH.ORIGINATORS. |
|
3.
|
Leave the Audited Record ID and Audited Fieldname fields blank. |
|
•
|
If running the report first thing in the morning, enter the previous day in the first Update date range field, and then enter T in the second field to indicate today's date. |
|
•
|
If running the report in the evening, enter T in both fields to see all changes made today. |
|
5.
|
Leave Optional Company ID blank. |
|
6.
|
Click F2-Create Report. |
|
7.
|
Make sure the bank account numbers are correct. These bank account numbers are where transfers would go for refunds, payments to the originators, and so on. |
Client Banking Information
|
1.
|
Select System Administration > File > Audit Control Maintenance > File Audit Reports > Find Changes to a File Report. |
|
2.
|
In the Audited Filename field, enter CLIENT.MASTER. |
|
3.
|
Leave the Audited Record ID field blank. |
|
4.
|
In the Audited Fieldname field, enter one of the following: |
|
•
|
To check your clients' ABA/Routing Numbers, enter ABA.NUMBER. |
|
•
|
To check your clients' Bank Account Number, enter BANK.ACNO. |
Note: Both of these numbers are maintained in the Client Details Billing tab in PrismHR.
|
•
|
If running the report first thing in the morning, enter the previous day in the first Update date range field, and then enter T in the second field to indicate today's date. |
|
•
|
If running the report in the evening, enter T in both fields to see all changes made today. |
|
6.
|
Leave Optional Company ID blank. |
|
7.
|
Click F2-Create Report. |
|
8.
|
Make sure that any changes are legitimate. |
Login History Report
The Login History Report records login history information including the time, date, and IP address used for the login. This report is useful to identify any unusual IP addresses used to log in to a user’s account.
|
1.
|
In PrismHR, click  (Reports). (Reports). |
|
2.
|
From System|Report, select Login History Report. The Login History Report opens. |
|
3.
|
You can use the following selection criteria and sort options to filter the report results: |
|
Identifier ID
|
Enter an identifier ID or click the link to select from a list.
|
|
Company ID
|
Enter a company ID or click the link to select from a list.
|
|
Employee ID
|
Enter an employee ID or click the link to select from a list.
|
|
User Database
|
Select a user database:
|
•
|
Prism Users (HRP.USERS file)
|
|
•
|
Webservice Users (WEBSERVICE.URSERS file)
|
|
|
Result
|
Select a result:
|
|
Start Date on or after
|
Enter or select a date for the report to start.
|
|
End Date on or after
|
Enter or select a date for the report to end.
|
|
Primary Sort
|
Select one of the following sort options:
|
|
Secondary Sort
|
See options for Primary Sort. The list shows all options except for the Primary Sort.
|
Sensitive Information Changes Report
In PrismHR, this report runs on the first calculation of a payroll. The process looks to see if any changes to sensitive employee information has changed since the last payroll run for the employee. This report is automatically generated.
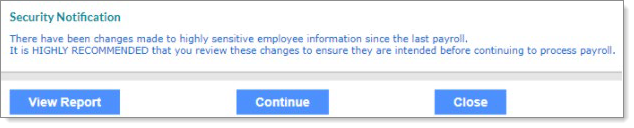
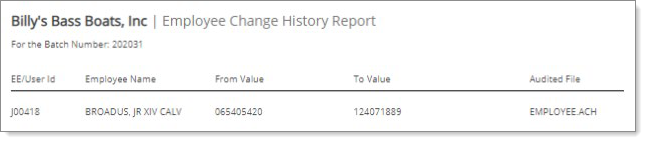
Click View Report. The changes to sensitive employee information since the last payroll run and the report displays. In the following example, the ACH Transit Number of an employee’s ACH entry was changed to a popular routing number used for cash cards.
Create Processes
Ongoing vigilance is the best practice to minimize the vulnerability of your organization and your clients. To ensure the safety of system information, establish best practices for your company and work with a security expert to mitigate your overall security risk.



